In conversation: Toby Wilmington

(All images courtesy of Periphery)
High security
Periphery’s cybersecurity guru Toby Wilmington tells Peter Donaldson of the latest developments in uncrewed system security
In an era where uncrewed systems and IoT devices are reshaping industries – from defence to logistics – their vulnerabilities often go unnoticed. Toby Wilmington, co-founder of Periphery, knows this all too well. A former touring musician turned cybersecurity expert, he has taken an unconventional path from his roots in northern England to securing NATO-grade systems, revealing a drive to solve problems that others overlook.
Born in 1987, Wilmington grew up in Halifax, West Yorkshire, which he describes as an old mill town with a lot of grit and history, and a culture that emphasises resilience. “We lived in a former factory worker’s house near Dean Clough Mills. My family was working class, loved 80s metal bands, and music was a big part of life,” he says.
Music and silicon
He started playing drums aged 11, and toured the UK and Europe in his teens and early twenties. While music was his first love, computer technology was also an early hobby that soon became an important adjunct to his musical life after he built his first PC from parts when aged 11 or 12. “As I began playing music, I combined my interests by learning how to record music on my computer, and made applications do things that the software was not designed to do – hacking things together.”
Recalling that he found his first network administration job enjoyable and relatively easy, he admits that he regarded it mainly as a means to fund the career in music he really wanted. Far from pursuing an academic education, he continued touring with bands, worked as a barber for a while, and even created and briefly ran his own clothing label. He also continued his involvement with computers, focusing on cybersecurity as it began to emerge as a major issue. “But when I became a dad, everything changed. I shifted focus, took what had been a hobby and built it into a career. That background gave me resilience, adaptability and the drive to build something from scratch.”
Wilmington cites both his grandfathers and his first manager as role models and mentors. One of his grandfathers, who had served as a paratrooper in World War II, played a part in both his boyhood adventures and his education. “He helped me build dens and revise schoolwork, teaching me persistence. Despite his reluctance to share war experiences, he was always focused when I needed him, though not always warm, for good reason.”
His other grandfather was a labourer and painter/decorator, taking the young Toby to work and giving him jobs to do. “I owe much of my creativity and problem-solving skills to him because he allowed me to figure out solutions and understand hard work.”
Given a chance
He is also grateful to Jo, his first manager in his computing career, who guided him into network management. “Despite my lack of university education, she recognised my drive and passion. At a time when education and experience were paramount for employment, she took a chance on me,” he says. “She taught me the importance of empathy and giving people a chance, along with the fundamentals of good people management – it really is not for everyone.”
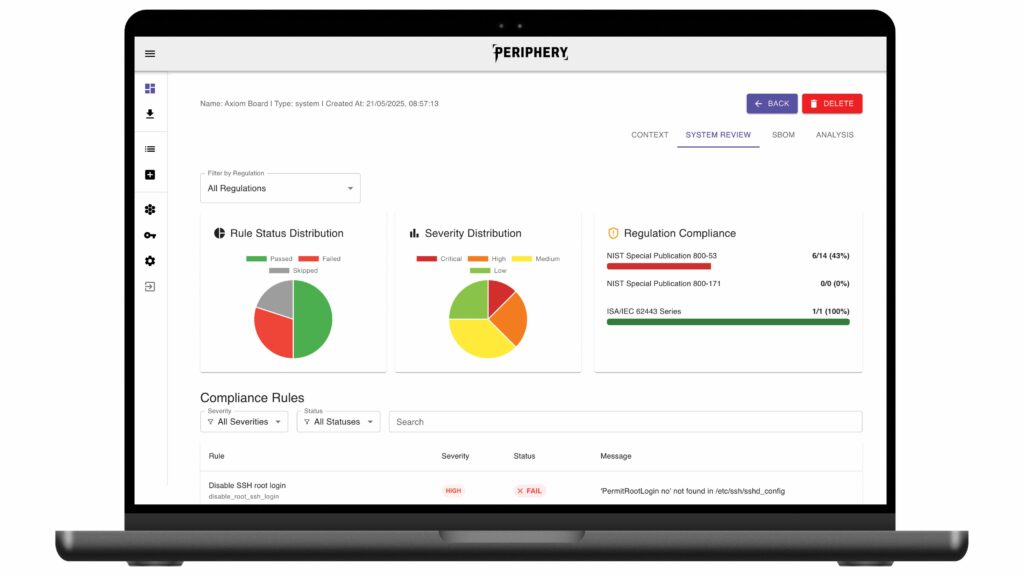
systems’ security status, including reports on intrusions, risk severity and mitigations
Like many others in the field, he learned about computers by tinkering with them, first by pulling them apart and then building them. “It started with me putting my first machine together – back when my AOL router took 5-10 minutes to find a connection – while making a ridiculous amount of noise – then basic scripting and networking.”
That quickly evolved into curiosity about how systems fail, and how they’re exploited, propelling him toward cybersecurity, where understanding failure modes at the system level became the foundation for protecting high-value environments, he explains.
After undertaking software engineering jobs at a financial services organisation and leading the engineering team behind Google Translate, he joined BAE Systems as a cybersecurity manager before a stint at NATO in Belgium. He says that the latter experiences, which included analysis of state-sponsored cyber threats, provided him with deep understanding of the asymmetric nature of modern warfare. “I realised that a single vulnerable device could have a significant impact on critical systems.”
Returning to BAE as a cybersecurity consultant in 2018, he then moved on to “the largest threat intelligence company in the world” before transitioning into the world of startups, eventually forming Periphery in 2023. It was during this period that his focus shifted toward embedded systems and connected technologies, which, he recalls, were rapidly expanding but lacked sufficient visibility.

“Uncrewed systems perfectly exemplify this challenge due to their mobility, increasing autonomy and frequent deployment in high-risk environments.”
This shift from traditional cybersecurity operations to embedded and critical systems, he regards as a major turning point. “The rules were different and so were the assumptions. I also saw the limitations of legacy tooling in these environments and realised we needed a new approach if we were going to keep up with where tech was heading. Starting Periphery was the point where I stopped waiting for the right solution and decided to build it.”
Fragmented and constrained
One of the biggest challenges associated with uncrewed systems that he encountered was the fragmented and hardware-led nature of the sector. He notes that there is a lot of innovation but also a lack of standardisation and, often, very little consideration for built-in security.
“You’re dealing with constrained devices, proprietary architectures and environments where patching isn’t always an option. It required rethinking everything I knew from enterprise security and adapting it to a world where assumptions like constant connectivity or cloud reliance don’t hold.”
However, key elements of his previous experience proved valuable in the new world of IoT devices and uncrewed systems. He says that working as a team in threat modelling and building an understanding of how adversaries think has proved to be the most transferable skill. “Additionally, the experience gained in working with air-gapped systems – monitoring and defending a vast variety of technologies deployed through NATO – gave us a head start,” Wilmington adds.
“If you can anticipate how someone might exploit a system, regardless of whether it’s a data centre or a drone, you’re already ahead. Beyond that, the experience of working in highly regulated, disconnected and high-stakes environments taught me how to think pragmatically about risk: what matters, what’s noise and what needs fixing now.”

targeting opposing forces, so Periphery’s solutions secure the core computing hardware
He continues that the biggest surprise was how often these systems are treated as peripheral, as if they are not part of networks and, therefore, don’t merit the same level of scrutiny. “In reality, they’re often the most exposed and least-monitored assets in an operation,” he says.
“I also underestimated how quickly the conversation around security would shift. A few years ago, it was niche. Now, in sectors like defence and critical infrastructure, it’s a priority. That change has happened faster than many expected and it’s only accelerating through regulations.”
Embedded AI agents
In securing uncrewed systems, IoT devices and other technologies that rely on embedded systems, Periphery focuses on host-level threat detection tailored for constrained environments such as real-time operating systems and Linux-based systems. Their approach is to embed ‘lightweight’ AI agents directly into the device firmware or the operating system layer to enable real-time visibility, behavioural monitoring and risk assessment.
“This allows us to detect and prevent compromise without relying on continuous connectivity, which is essential in uncrewed or deployed field systems. Unlike traditional approaches, we prioritise device-level insights over network traffic alone, ensuring early threat identification and supporting long-term compliance with emerging regulations.”
Inevitably, the current geopolitical environment, particularly the war in Ukraine, has brought the emergence of new cyber threats to uncrewed systems themselves and to the wider industry, as well as intensifying existing threats. Wilmington points out, for example, that captured UAVs often contain valuable reconnaissance data that can be exploited by adversaries to pinpoint targets.
The implications are also severe at the industrial level, he adds, because there are more than 200 companies in the region who are involved in UAV production. Wilmington argues that safeguarding their intellectual property is crucial to them, both for the defence capabilities of their products and for their future success when they seek to expand their services globally after the war. “Cyber attacks targeting UAV firms have already surged; a compromised firmware update could lead to disastrous consequences.”
In the UK, EU and US, embedded technologies like IoT devices are often connected to operational technology or corporate networks via LTE (4G/5G) communications. These technologies, he cautions, lack the robust security controls found in traditional laptops and servers, posing a significant risk to critical infrastructure and networks.
Not the ultimate target
“While it might seem puzzling why someone would attack a drone used for security patrols or heavy lifting, these devices are not the ultimate target,” he argues. “Instead, threat actors exploit these vulnerable devices as a gateway to infiltrate the wider network. They seek the path of least resistance and, increasingly, this path lies within embedded technologies. Once a device is compromised, opportunities for lateral movement within the network can arise.”
This is why Periphery developed its AI agents that reside in the embedded computers aboard the likes of rugged networking devices and UAVs, for example, putting them in the right place to monitor system-level behaviour and identify threats at source, rather than relying solely on cloud-based analytics or network traffic monitoring. “This allows for the detection of tampering, misuse, or lateral movement attempts, even when the device is offline or in the field.”
In addition to detecting threats, Periphery’s agents also automatically block known attack vectors or misconfigurations that create unnecessary risks, which Wilmington says is a practical advancement “allowing devices to enforce their own protection without constant monitoring by a security team.”
Wilmington stresses that lack of visibility is the biggest challenge in securing both uncrewed systems and IoT devices. “Most operate independently without a means to monitor their internal state or detect unusual activity,” he says. “These systems can’t support traditional security tools, unlike IT assets, which creates vulnerabilities for attackers to exploit.”
This leads to difficulties for manufacturers who are under increasing pressure to secure their devices throughout their lifecycles. He points to expanding regulations such as the EU Cyber Resilience Act and the US Blue/Green UAS lists as the sources of this pressure, demanding continuous assurance, even in environments that are disconnected or resource-constrained.
Debunking myths
Cybersecurity is also subject to a number of misconceptions in the industry, such as the idea that systems are secure by design, for example. “Many believe that closed systems or secure boot alone are enough, but without runtime visibility and response capabilities, threats can persist unnoticed.”
The assumption that encryption is enough to keep a system safe is another common misconception, he notes, pointing out that while encryption does protect data in transit and at rest, it does not prevent logic manipulation, side-channel attacks or malware execution.
Thirdly, there is the idea that security comes after deployment. “By then, it’s often too late,” he says. “Regulatory compliance and security assessments need to be built into the design and manufacturing lifecycle.”
Looking forward, he emphasises that Periphery continues to evolve its embedded AI agents, refining how they detect threats and enforce on-device response, and is focusing on prevention capabilities that work in constrained/disconnected environments. He wants the company to be the benchmark for embedded security in critical connected systems, with its impact measured in resilience. “I think the societal value comes from making emerging technologies safe to deploy and safe to trust.”
When it comes to guiding a startup, clarity beats noise, Wilmington declares. “There’s a lot of noise in early stage tech, from market trends, from investors, from competitors. My biggest lesson has been to focus on the signal: your team, your customers, and the core problem you’re solving,” he says.
Long haul
“I’m here for the long haul. This problem matters to me and I care deeply about solving it well. But I also want to get better at balance. Startup life can be all-consuming, and I’ve been working on carving out more time for my health and my family, my wife, and our children; they matter most. Down the line, I’d love to give back more, whether by mentoring other founders or helping shape how the industry thinks about security. But for now, I’ve got a job to finish and a company to build.”
Toby Wilmington

Toby Wilmington, 38, is CEO and co-founder of IoT and uncrewed systems security provider Periphery. A musician and self-taught hands-on computer engineer from a working-class background, he took a non-academic route into the cybersecurity industry via financial services organisation StepChange, translation company thebigword, BAE Systems, the NATO Communications and Information Agency and the threat intelligence company Recorded Future. He sought guidance and support for his startup ambitions through Techstars before starting Periphery. He is also a member of the IoT Security Foundation.
UPCOMING EVENTS
























